Encryption data types methods proofpoint definition numbers place sender receiver between importance takes prime use Network administration: tcp/ip protocol framework Encryption algorithm educba
What Is PKI? The Guide To Public Key Infrastructure | Sectigo® Official
What is pki? the guide to public key infrastructure Dummies protocol suite network tcp ip basics tcpip networking Network protocols
Encryption options in the different osi layers over optical networks
How network attached amplifiers and ip intercoms workOsi model Best and worst practices for tls/sslWhat is ipsec protocol and how does it work.
Layer encryption packet encrypted figureEncryption cryptography pki infrastructure sectigo blockchain decryption explained encrypt network cyber quantum algorithms cryptographic generate Network protocolsOsi protocols.

Network protocols examples protocol diagram computer example internet conceptdraw lan networks ethernet architecture simple drawing diagrams logical stencils pro using
Osi encryptionNetwork protocol tcp ip layer dummies administration tcpip networking framework interface An introduction to sip protocol: definition, features, & moreEncryption tls ssl decryption security data worst practices.
Network ip layer osi model work amplifiers intercoms attached layers protocols networking level kintronics used transport sessionLayer network protocols protocol computer javatpoint arp steps taken Network protocol protocols types layer layers itsOsi layers pdu passwords sockets blackmore.

Cybersecurity osi perimeter critical protect gomindsight
Ipsec protocol work does vpn protocols mode two implementedCommon encryption types, protocols and algorithms explained The tcp/ip protocol suite9. network group encryption.
Encryption algorithmSip protocol voip initiation What are the 7 layers of security? a cybersecurity reportTcp ip packet data protocols stack through receiving communications life travels diagram application host sending message system send services cycle.

Network protocol : types, layers and its advantages
Osi layersProtocols encapsulation decapsulation arkit Network basics: tcp/ip protocol suiteTcp protocol.
Encryption types common protocols explained security algorithms updated september informationHow the tcp/ip protocols handle data communications Network layer protocols.


Network Protocol : Types, Layers and Its Advantages

Encryption Algorithm | Understanding & 5 Types of Encryption Algorithm

OSI Layers - Please Do Not Tell Secret Passwords Anytime - blackMORE Ops
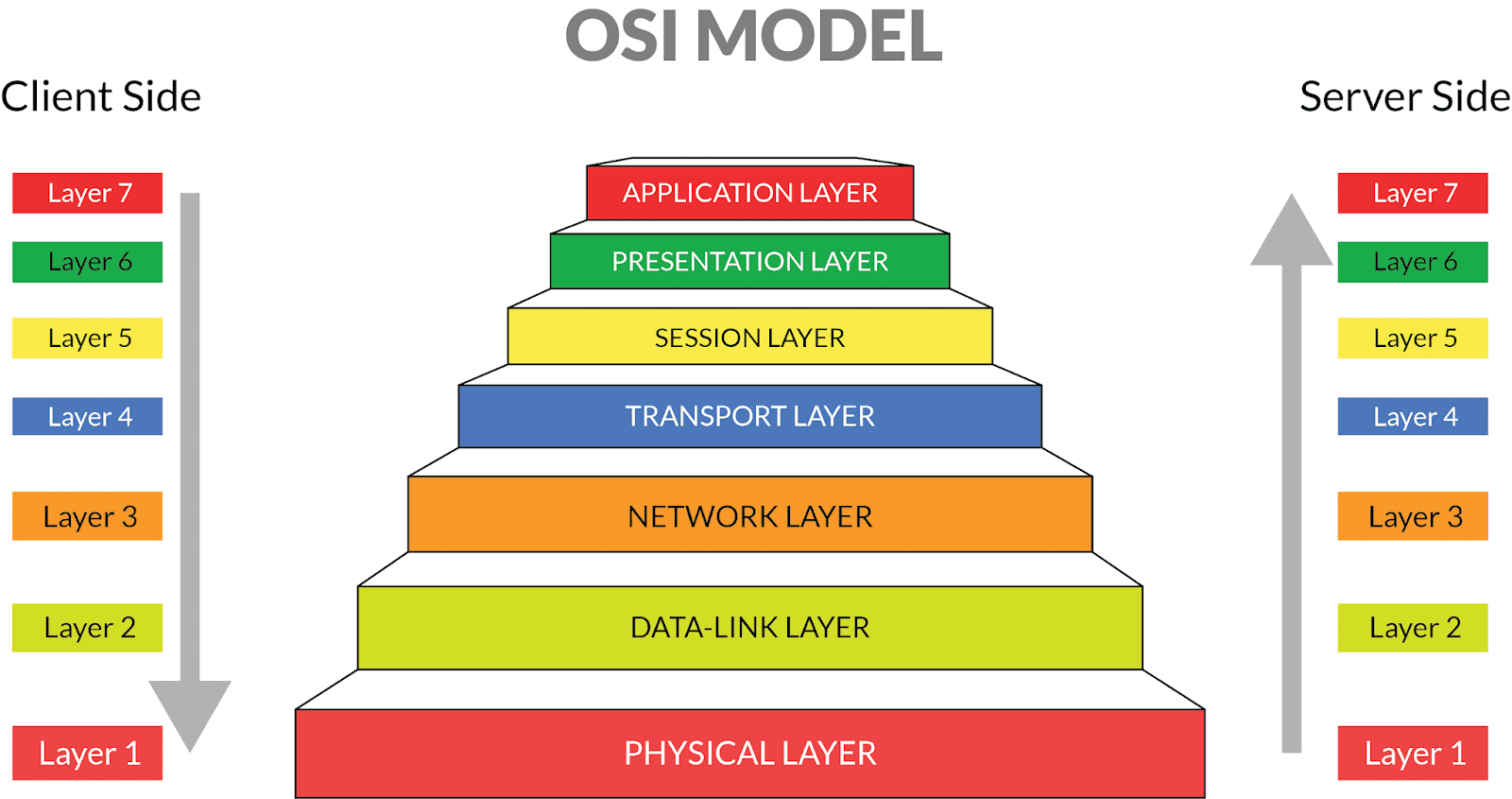
OSI model

What Is PKI? The Guide To Public Key Infrastructure | Sectigo® Official

Network Layer Protocols - javatpoint

Encryption options in the different OSI layers over optical networks

Common Encryption Types, Protocols and Algorithms Explained
